
If you own a computer, it is imperative that you take care of its security by investing time and resources in safeguarding it. Threat actors across the world are constantly working on undermining the security measures of computers. It doesn't matter whether you are an individual or a big corporation raking in millions in revenue; you should be on guard.
There used to be a time when operating systems like Windows and macOS were the most bountiful targets for such perpetrators, but they are not the only prey now.
Thanks to an increase in both personal and enterprise usage, Linux distributions are slowly but surely becoming the next big thing to crack. And guess what? A new threat called “Bootkitty” has recently been uncovered that targets UEFI-equipped Linux systems.
Bootkitty: Should Linux Users Be Worried?
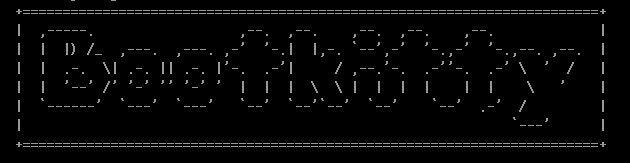
Known for their cybersecurity expertise, ESET's researchers first stumbled across this on VirusTotal where it was uploaded anonymously as an unknown UEFI application named “bootkit.efi”.
After analyzing it, the ESET team found that it was a UEFI bootkit for Linux, which targeted specific versions of Ubuntu.
If you didn't know, a bootkit is a type of rootkit that is specifically designed to infect a computer's boot process. These allow an attacker to carry out a range of malicious actions while staying hidden from conventional malware removal methods.
The researchers deduced that Bootkitty's main goal was to:
Disable the kernel’s signature verification feature and to preload two as yet unknown ELF binaries via the Linux init process.
As it stands, Bootkitty can affect UEFI systems with secure boot enabled only if the attacker has successfully installed malicious certificates, and also in cases where secure boot is not enabled.
The researchers found many artifacts that aided them in understanding what this bootkit was all about. They found two unused functions that were capable of printing special strings during execution.
The first was the ASCII art you saw above, which led ESET to believe that Bootkitty is what the bootkit is called.
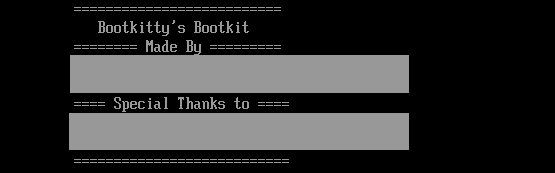
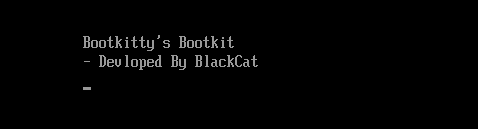
Source: ESET
The second was the printing of a list of potential Bootkitty authors (redacted by ESET) and other people related to the malware, with another set of strings being printed out on every boot containing the following text:
Bootkitty's Bootkit
- Developed By BlackCat
ESET clarifies that they don't believe this is related to the notorious BlackCat ransomware group, as that group primarily develops Rust-based malware, while Bootkitty was developed using C.
Currently, many in the cybersecurity space consider Bootkitty to be an initial proof-of-concept bootkit, with ESET explaining that according to their data, it has not yet been used in the outside world.
So, for now, there is no need to panic. 🤓
Nevertheless, taking some preventative measures will go a long way in securing your Linux system. You can learn about some of those by reading on.
Don't Miss The Deals 🕐

What Steps To Take?
For starters, keep secure boot enabled, as it is highly unlikely that your system has been affected by the Bootkitty attackers' malicious UEFI certificates. Then comes the most obvious one: Keep your Linux distros updated with the most recent patches; upgrade if you are running something ancient/unsupported.
Additionally, ESET mentions to always keep your UEFI revocations list updated to prevent malicious bootloaders from loading and compromising your system. You could also follow some tips mentioned in our article to improve the security of your Linux system.
If you are interested in learning more about the inner workings of Bootkitty, I highly suggest you read ESET's deep dive blog.
For samples and the indicators of compromise (IoCs), you can visit ESET's GitHub repo.
Suggested Read 📖

- Even the biggest players in the Linux world don't care about desktop Linux users. We do.
- We don't put informational content behind paywall. Your support keeps it open for everyone. Think of it like 'pay it forward'.
- Don't like ads? With the Plus membership, you get an ad-free reading experience.
- When millions of AI-generated content is being published daily, you read and learn from real human Linux users.
- It costs just $2 a month, less than the cost of your favorite burger.
Become a Plus Member today and join over 300 people in supporting our work.










