When you install Linux on your UEFI-enabled computer, you have to disable Secure Boot because the live USB will refuse to boot with the option enabled.
Some mainstream Linux distributions support Secure Boot, but it is still challenging to set up for many other distributions (and with Nvidia hardware onboard).
While things may not have improved over the years, Secure Boot is an essential protection feature in general.
So, for the sake of convenience and make users aware of it, GNOME and Red Hat developers are working on notifying (or warning) the user if Secure Boot is disabled, as spotted by Phoronix.
How is it Useful?
UEFI/Secure boot has been criticized for the DRM as it takes away the freedom from users. Many in the open source community still disagree with the implementation of UEFI/Secure Boot and TPM as it came as an inconvenience. This has given birth to projects like Coreboot, flourishing in the open-source world.
Of course, I would advise you to purchase new hardware with Coreboot support if you daily drive Linux, which is a different story.
That said, it is safe to mention that Secure Boot is the easy way out.
Secure Boot’s security is still debatable, considering the proprietary firmware bundled. But, it is a fundamental protection mechanism to secure the system’s firmware.
So, the developers are preparing to show the warnings in Plymouth (boot splash screen), GNOME Display Manager (GDM), and GNOME Control Center.
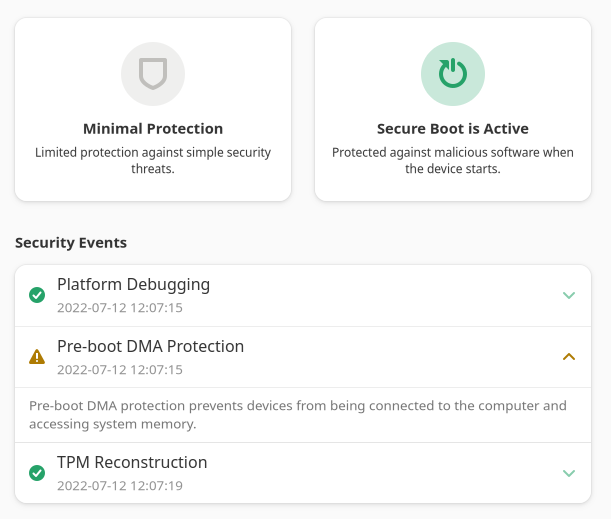
One of the GNOME developers shared more details on it in a blog post while sharing some of these screenshots.
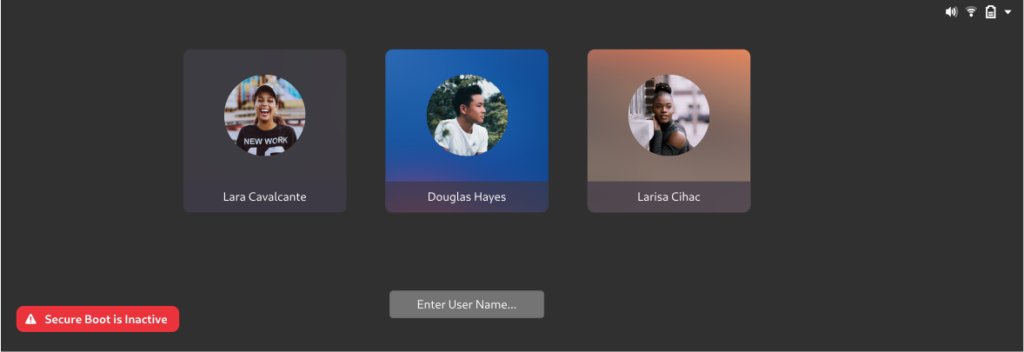
A Red Hat developer mentions in the merge request:
Secure boot is used against several security threats when malware tries to infect the firmware of the system. Users may inadvertently disable or software may intentionally disable the secure boot. Consequently, the system is running on an insecure platform with incorrect configuration. If Plymouth could offer a warning to the user, the user could reboot and reconfigure their system or asks for help immediately.
So, as a GNOME user, I think it should be interesting to see the difference it makes when it gets to the final release of GNOME 43 or any future releases.
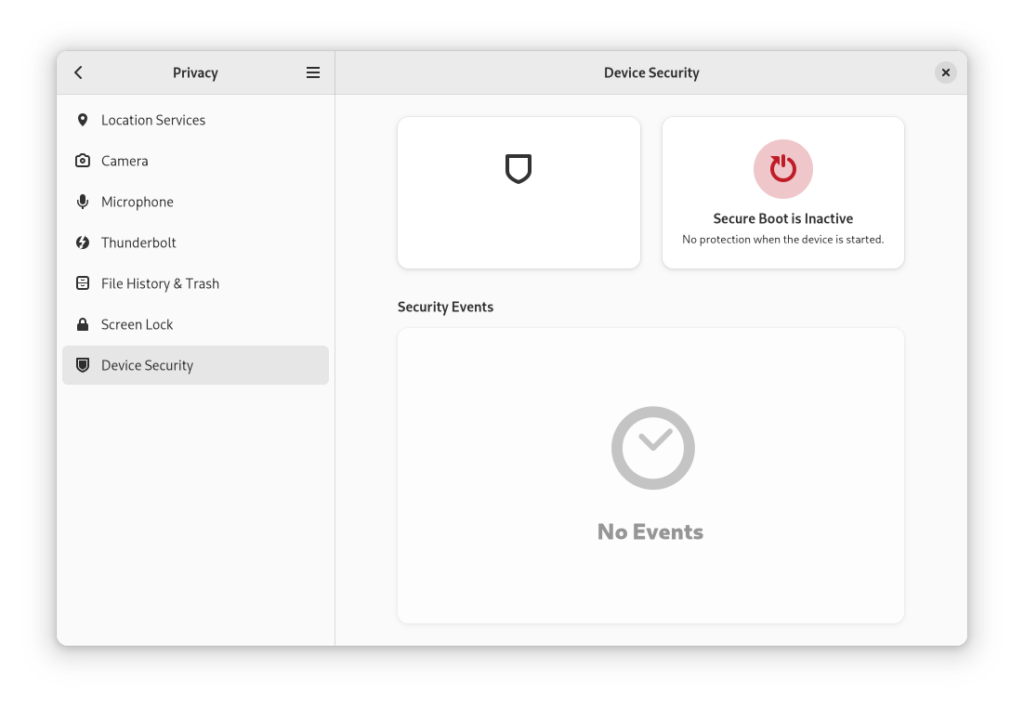
If you are curious, you can find this option under the Device Security section of the Privacy tab in GNOME Control Center, as shown in the screenshot below of my system running GNOME 43 alpha on Arch Linux:
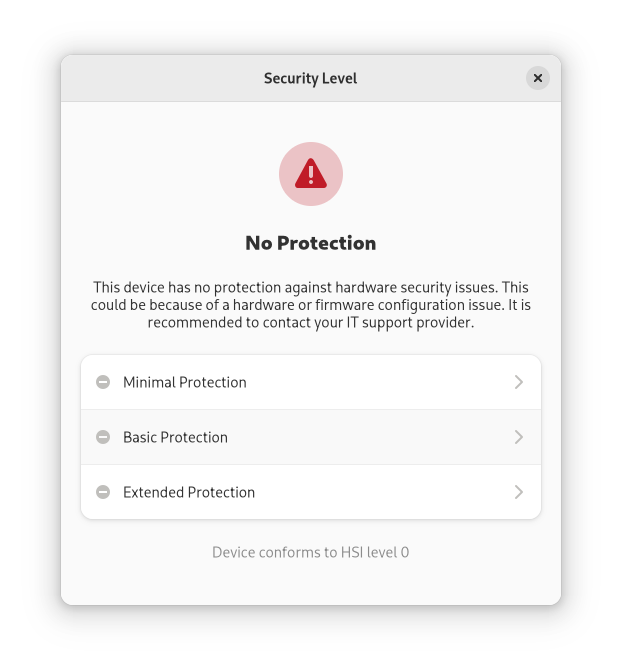
The menu can also show TPM, Intel BootGuard, and IOMMU protection details:
It seems my system is not as secure as I thought… But maybe that’s the point of this feature?
If you only used UEFI mode with your Linux distribution and had the protection features disabled for convenience, could this make you aware of it?
Probably. But, looking at the state of Linux distributions and the issues with enabling secure boot. I’m not confident if it would be that big of a deal. We shall find out soon.
How to Disable the Warnings?
As mentioned in the merge request on GNOME Gitlab, adding sb-check=false to your kernel parameters will disable all these warnings.
You do not need to worry about it as an end-user, though.
What do you think about this upcoming feature addition to GNOME 43 or later? What is your opinion about UEFI/Secure Boot?
More from It's FOSS...
- Support us by opting for It's FOSS Plus membership.
- Join our community forum.
- 📩 Stay updated with the latest on Linux and Open Source. Get our weekly Newsletter.