
Malware targeting cryptocurrency users has increased sharply over the past year. Malcious actors now focus on browser-based tools, knowing they often store sensitive wallet data and private keys.
Browser extensions have become a key attack surface. Many are trusted by people without a second look, giving attackers a direct line to credentials and activity.
Fake wallet extensions, phishing websites, and info-stealing malware are all being deployed together. All of this suggests a broader shift toward multi-vector attacks aimed at draining crypto assets.
One such campaign was recently uncovered, involving malicious Firefox browser extensions and malware used to compromise users and steal over $1 million in cryptocurrency.
GreedyBear is An Unruly Carnivore
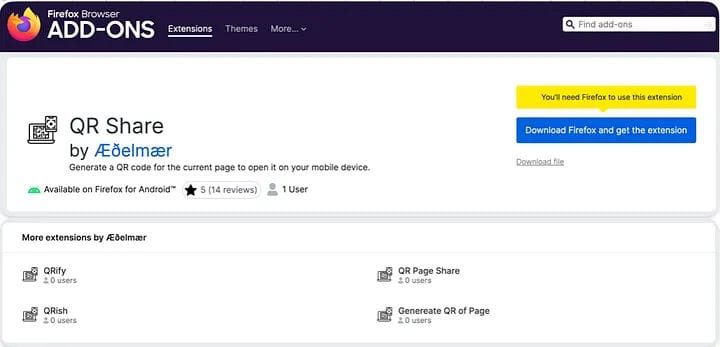
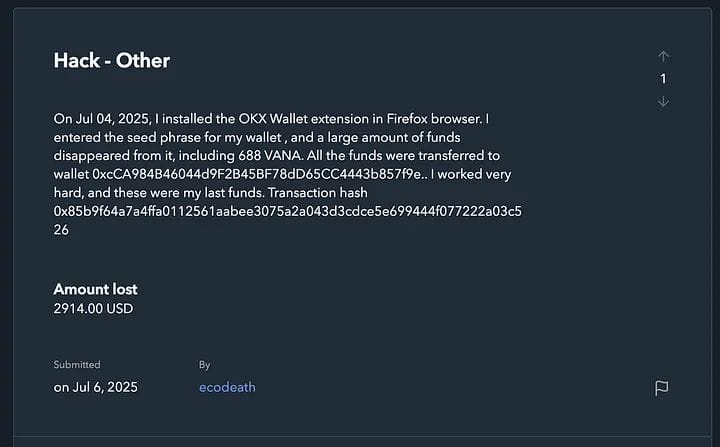
Source: Koi Security
Koi Security investigated a coordinated attack named GreedyBear, involving over 150 malicious Firefox extensions designed to impersonate crypto wallets and silently steal user credentials and digital assets.
The campaign operated across three attack methods: malicious browser extensions, phishing websites, and desktop malware payloads. All three vectors worked in parallel to maximize success and avoid detection.
The extensions posed as legitimate wallets like MetaMask and Exodus. Once installed, they logged sensitive inputs, extracted wallet phrases, and captured IP addresses during user interaction.
The malicious extensions and malware all communicated with a single command-and-control (C2) server. Koi Security traced this activity to the IP address 185.208.156.66, which acted as the central hub for data collection and attacker control.
Koi Security researchers also warn that the same group is now preparing to target the Chrome Web Store using the same tactics. A wave of fake wallet extensions may be launched soon if not stopped.
Speaking about this, Tuval Admoni, security researcher at Koi Security and former cyber analyst and project leader in the IDF’s Unit 8200, stated that:
This isn’t a passing trend — it’s the new normal. As attackers arm themselves with increasingly capable AI, defenders must respond with equally advanced security tools and intelligence. The arms race has already begun, and legacy solutions won’t cut it.
- Even the biggest players in the Linux world don't care about desktop Linux users. We do.
- We don't put informational content behind paywall. Your support keeps it open for everyone. Think of it like 'pay it forward'.
- Don't like ads? With the Plus membership, you get an ad-free reading experience.
- When millions of AI-generated content is being published daily, you read and learn from real human Linux users.
- It costs just $2 a month, less than the cost of your favorite burger.
Become a Plus Member today and join over 300 people in supporting our work.










