
It’s evident that security for anything is a top priority now. And, ensuring that the software you use is genuine and developed by the original developers is even more important.
Of course, there will always be pirated or modded software available but even with that, if they utilize code signing, you will be able to verify the source (if you trust them in the first place).
Even though software signing is important and has a ton of benefits to ensure the integrity of the software, code signing isn’t something adopted by many developers.
So, to encourage them to easily sign their software along with other benefits, The Linux Foundation teamed up with Google and Red Hat to announce – “Sigstore“, which will be a free-to-use Open-Source software signing service to easily let developers sign their software and let their users verify the integrity through a public log.
Sigstore: What is it? How is it Useful?
To quickly understand what it is, Google explains in their blog post:
Just like how Let’s Encrypt provides free certificates and automation tooling for HTTPS, sigstore provides free certificates and tooling to automate and verify signatures of source code.
So, if you’re aware of Let’s Encrypt, you should have a faint idea on what sigstore is all about.
And, it is not the only open-source code signing software/service.
There are many open-source code signing software that already exist. However, the tools available for that aren’t as good, presents many challenges to the developer, or it is simply unknown to the developers.
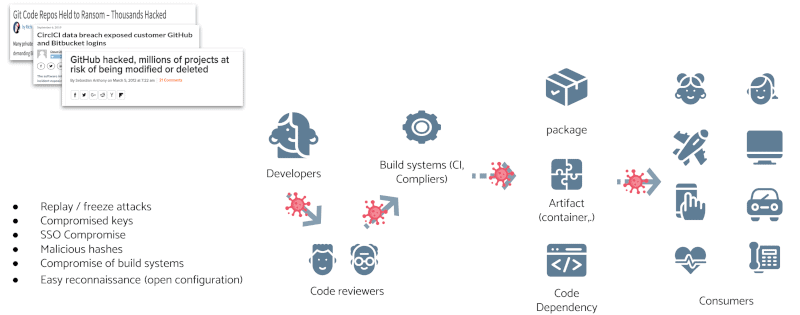
With this project, they aim to offer a secure software signing service to improve the open-source software supply chain and avoid SolarWind-like security disasters. Theoretically, it should help project maintainers save time but still secure their open-source software supply chain.
Sigstore will rely on short-lived key pairs using the sigstore client tooling – hence, a better security eventually.
Not just limited to empowering developers with software signing services but also ensuring a tamper-proof public log to verify if/when it was originally signed by the developer.
Some project maintainers end up managing public keys in their git repo, which isn’t totally secure either.
But, with sigstore, once the signing is complete, you may discard the keys, and it won’t require you to manage the keys. All the certificates will be recorded in a tamper-resistant public log.
On top of it, OpenID Connect protocol will be utilized to verify and secure the identities of the software author. So, you can check the log to see the details and verify the integrity of the software.
As mentioned in their official website:
We are initially targeting generic release artifacts such as tarballs, compiled binaries and container images. Later we will explore other formats (such as jars) and manifest signing, such as SBOM etc. We also open to collaborate with package managers and ease the adoption of signing for their communities.
Almost every tool is available for general use, but it’s being constantly developed, tested, and improved as you read this. So, feel free to check out their official website for the current project status and explore the available tools.
Closing Thoughts
I’d say that it is a fantastic initiative and the open-source software community definitely needs this.
Depending on how the project progresses and improves, we’ll know if it truly solves the problems it aims to address.
Of course, no code signing service can prevent malicious intent of a software author. So, just like every website secured with HTTPS does not mean it’s safe to use completely, you will still have to keep an eye on how a software behaves after verifying the integrity of the software.
What do you think about sigstore? Personally, I appreciate the initiative of an open-source code signing service that tries to tackle multiple issues in a software supply chain, feel free to let me know your thoughts in the comments.
More from It's FOSS...
- Support us by opting for It's FOSS Plus membership.
- Join our community forum.
- 📩 Stay updated with the latest on Linux and Open Source. Get our weekly Newsletter.







