
Ubuntu 25.10 was released earlier this month, bringing with it many improvements like a recent kernel with extended hardware support, GNOME 49 with lockscreen media controls, new default core apps, and the removal of the X11 session.
It also included a major new Rust component called sudo-rs, which replaces the traditional sudo with a Rust-based alternative. But, so far, we have seen a major bug breaking flatpaks on this release, and while it was quickly fixed, another one was recently caught.
Oxidation Exposes Flaws
Ubuntu's oxidation is not new news; it has been going on for a while now, and it was expected that this move would run into issues; we have already seen a few cases already. Luckily, the latest one was caught in time and promptly fixed.
The bug was in the Rust-based date command, specifically with the -r option. This option is supposed to show when a file was last modified, but instead, it was returning the current date every single time.
So if you ran date -r /path/to/file, instead of showing the file's actual modification time, it would just show today's date. This might seem like a small quirk, but it had significant consequences.
Ubuntu's automatic update system relies on date -r to check timestamps. It looks at a reference file to see when the last update check happened. But since the command was always returning "now," the system never realized it needed to check for updates again.
The result? Ubuntu 25.10 systems stopped automatically checking for software updates. Manual updates still worked fine; you could run sudo apt update or open Software Updater without any issues. But the background automation bit was completely broken.
This also affected backups. The original bug reporter, fprietog, discovered their automated daily backups had stopped running. Since date -r made old backups appear as if they were done "today," the backup script never triggered, and there were no error messages to indicate anything was wrong.
Once developers realized the bug affected Ubuntu's own update mechanism, it was quickly bumped to critical priority and fixed.
Here's the Fix!
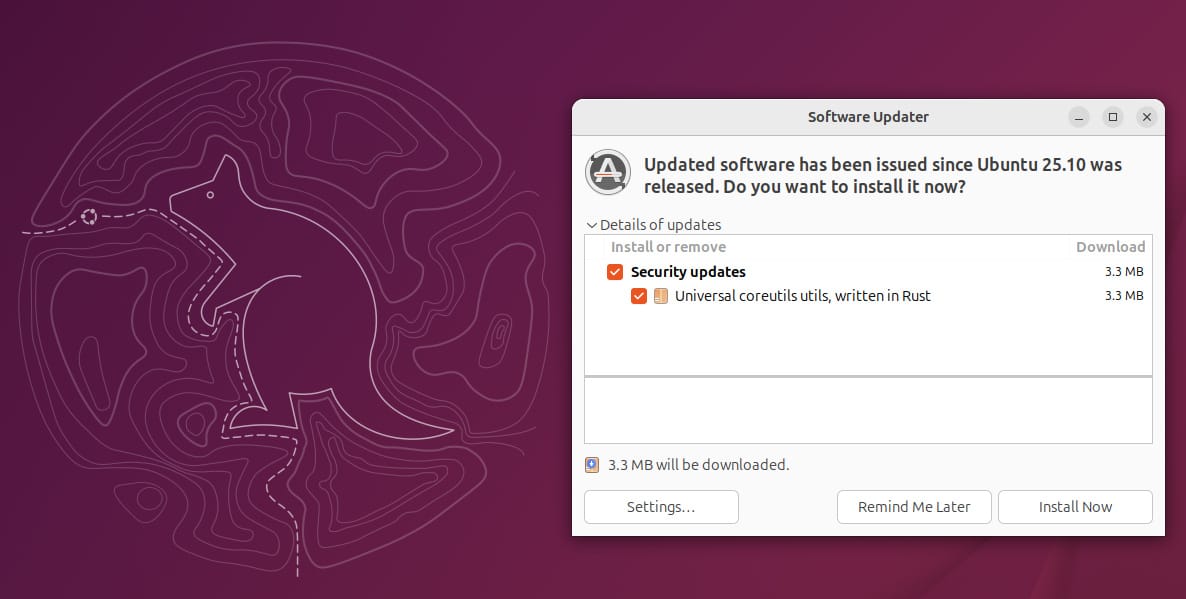
Getting this fix is quite straightforward. You can either go into Software Updater by launching it from the application launcher and applying the latest security updates that include this crucial patch for uutils coreutils.
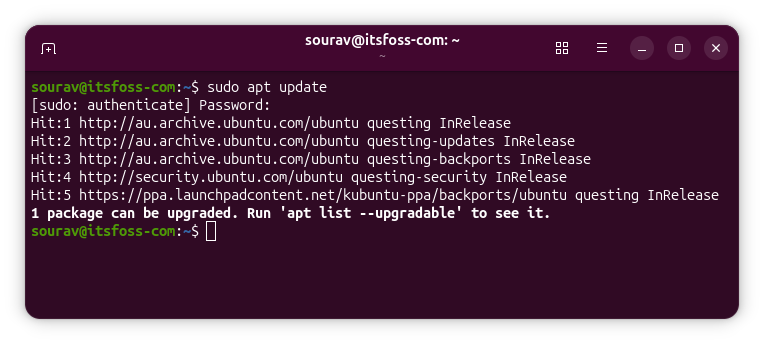
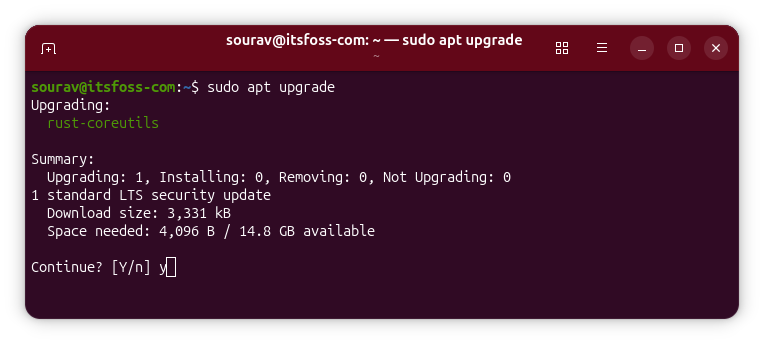
Or, you can run the following commands one after the other to get the patch:
sudo apt updatesudo apt upgradeVia: OMG! Ubuntu
Suggested Read 📖

- Even the biggest players in the Linux world don't care about desktop Linux users. We do.
- We don't put informational content behind paywall. Your support keeps it open for everyone. Think of it like 'pay it forward'.
- Don't like ads? With the Plus membership, you get an ad-free reading experience.
- When millions of AI-generated content is being published daily, you read and learn from real human Linux users.
- It costs just $2 a month, less than the cost of your favorite burger.
Become a Plus Member today and join over 300 people in supporting our work.











