
The XZ Utils backdoor discovery in March 2024 sent shockwaves throughout the Linux community. A developer known as "Jia Tan" had spent two years building trust before inserting malicious code into widely used compression libraries.
The backdoor targeted SSH servers by hooking into OpenSSH's cryptographic functions through the liblzma.so library. It's reach was so broad that major Linux distributions, including Debian, Fedora, and OpenSUSE, inadvertently distributed the compromised packages to their users.
Within hours of discovery, security researchers scrambled to understand the full scope of the supply chain attack. Now, over a year later, new findings show the backdoor's persistence in unexpected places.
What's Happening: Binarly researchers found 12 official Debian Docker images on Docker Hub that still have the XZ Utils backdoor. These bad containers have been sitting there for over 15 months.
The infected images mostly come from March 11, 2024, when the backdoor was in play. They include different Debian versions like unstable, testing, and trixie that got built during the attack.
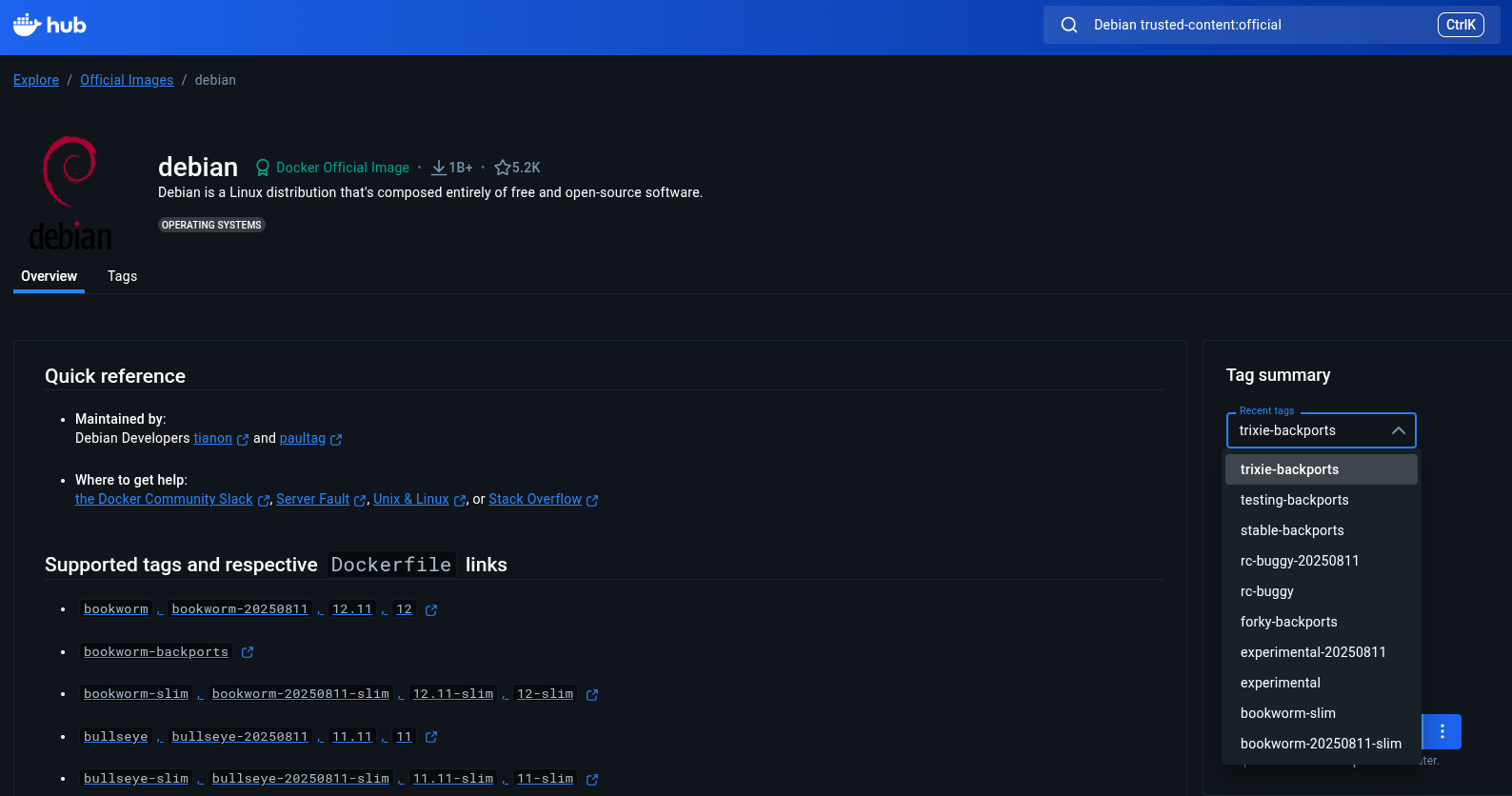
The team found 35 more images built using these bad base images, which exacerbate the problem further. Moreover, Binarly only looked at Debian containers, so other Linux distributions might have the same issue.
What Now: Binarly told Debian maintainers about the backdoored images and asked them to remove the affected images. The Debian team said no, saying the containers are too old and not really dangerous.
Tianon Gravi of the Debian development team put it like this:
So, given the wafer thin vectors of attack here, the extreme age of the images in question, and the fact that even at the time that they were fresh, they were images that shouldn't be used in production anyhow (Debian's "development" repositories), we've opted to leave them in place.
Debian says the affected images were just development builds that nobody should use in real systems anyway. They believe people should use newer, clean container versions instead.
Binarly kind of agrees but still thinks having backdoored images available creates risks. If you ask me, the whole thing shows how supply chain attacks can stick around in container systems way longer than expected.
Suggested Read 📖
- Even the biggest players in the Linux world don't care about desktop Linux users. We do.
- We don't put informational content behind paywall. Your support keeps it open for everyone. Think of it like 'pay it forward'.
- Don't like ads? With the Plus membership, you get an ad-free reading experience.
- When millions of AI-generated content is being published daily, you read and learn from real human Linux users.
- It costs just $2 a month, less than the cost of your favorite burger.
Become a Plus Member today and join over 300 people in supporting our work.











